You might think your organization doesn’t need a data security policy. All cybersecurity countermeasures protect data, don’t they? Yes and no. Data is important enough to merit its own dedicated security policy. Without one, you are vulnerable to costly attacks, regulatory penalties, and reputation damage. A thorough data security policy helps you avoid these negative outcomes. It forms the foundation for trust, compliance, and operational security.
The cyber threat environment certainly isn’t getting any less forgiving when it comes to protecting data. Data breaches in the third quarter of 2024 exposed more than 422 million records worldwide. Regulations affecting data security are also strict—and expensive if you don’t comply.
While IBM/Ponemon research says that a data breach costs $4.88 million to remediate on average, the numbers can get a lot more frightening than that. Meta paid $1.3 billion to settle EU data privacy violations in 2023. Amazon paid $877 million in a similar settlement in 2021. And, you’re probably thinking, if companies as well run and tech-savvy as Meta and Amazon can have data security problems like that, what am I doing about it? That’s where having a data security policy comes in.
What Is a Data Security Policy?
The term “data security policy” may be a little confusing, partly because any number of security policies related to data could be called “data security policies,” e.g., always encrypting data at rest. When an organization has a data security policy, sometimes called a data protection policy, it’s referring to a set of policies, practices, and controls that collectively have the goal of protecting the organization’s data from breach and other types of damage, such as ransomware.
A data security policy is often broad in scope, covering how data is handled, who is responsible for various data sets, and who can access them. These issues are more relevant than ever now that cloud computing and software-as-a-service (SaaS) have become so commonplace. Data security policy overlaps with data governance, which is about ensuring data availability, security, and quality. Data security policy also embodies the many controls and steps required to protect data and maintain regulatory compliance.
Why Does Your Organization Need a Data Security Policy?
Do you need a data security policy? Yes, and for several compelling reasons. The biggest driver of need is the confluence of rising data volumes, the distribution of data across multiple cloud platforms, and serious cyber threats and compliance requirements. These four forces combine to make it effectively non-negotiable that your organization have a coherent and thorough data security policy.
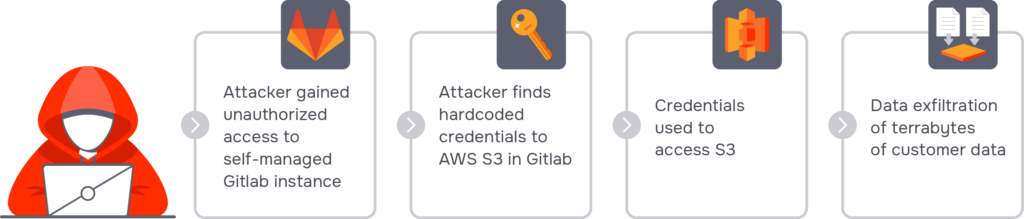
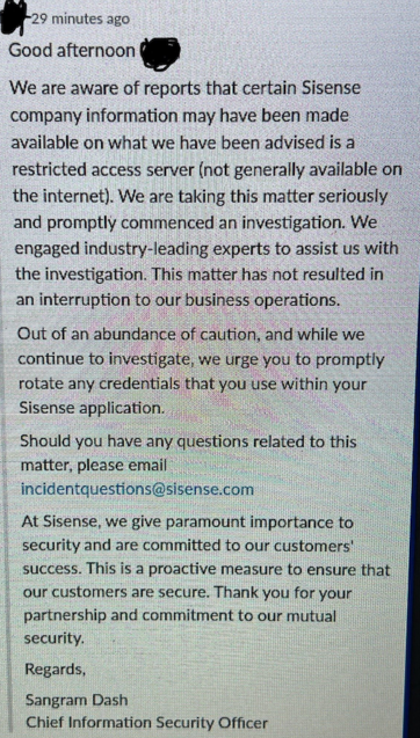
Of these issues, the proliferation of cloud and SaaS platforms is arguably the most serious challenge to data security. Employees now routinely store documents containing sensitive data on cloud volumes like Google Drive, often with open sharing settings. Notable SaaS data breaches include a 2023 hack of the Microsoft cloud that affected US government agencies.
The average business now has over 100 SaaS apps running, each of which can contain sensitive data—without anyone quite knowing where it all is. And, that’s not even considering the problem of “shadow SaaS,” which occurs when employees set up SaaS instances on their own without informing the IT department or security team.
All these factors add up to substantial data risk exposure. The stakes are certainly high. Data breaches are expensive to handle. They can trigger legal and regulatory problems that are costly to resolve, with fines for GDPR violations, for example, reaching into the millions. They disrupt business operations and potentially damage brands.
Done right, a data security policy goes a great distance to mitigating these risks and bolstering your overall security posture and compliance, including:
- Strengthening trust with customers and partners
- Facilitating proactive threat mitigation
- Strengthening the security of the SaaS ecosystem
- Aligning business operations with regulatory frameworks
- Reducing exposure from shadow IT and shadow SaaS
- Optimizing data governance and ownership
- Enables advanced incident containment strategies
- Supporting vendor risk assessments and monitoring
- Establishing a resilient compliance posture
7 Must-Haves for Every Data Security Policy
A sound data security policy comes to life through a collection of activities, workloads, and processes. It’s a good news/bad news situation. The good news is that many elements of a good policy already exist in your organization. For instance, you already have access controls. The bad, or at least challenging news is that you must align these elements, which may originate in multiple departments, with the data security policy, e.g., do your access controls support the objectives of the data security policy? With that in mind, here are seven “must haves” for every data security policy.
#1 – Comprehensive Data Inventory
A data security policy must be rooted in a comprehensive data inventory, which asks two basic questions: What data does your organization have? Where is it stored?
Both questions are deceptively simple. Regarding the data you have, this should include structured data found in databases and unstructured data, e.g., PDFs. Unstructured data might also comprise emails, instant messages, and rich media like audio and video recordings. You will almost certainly need an automated tool to discover all the data in your organization and its cloud instances.
Regarding where your data is stored, remember that the honest answer is “Almost anywhere, including places we haven’t thought of.” With a SaaS data discovery tool like Suridata, you can automatically scan numerous SaaS applications and find data that needs protection under the data security policy.
A related question is, “Who owns the data?” Each dataset in the inventory should ideally connect with a person or team responsible for maintaining data quality and following data lifecycle policies, e.g., deleting data over seven years old if that’s the rule.
#2 – Risk Assessment
With the data inventory in hand, you can now assess the risks each data set faces. You can take your choice of approaches to a data risk assessment, but the purpose is always the same: determining which data assets are at the highest risk for breach, and the impact of a breach. This requires ranking data by sensitivity and value. For example, a customer list may be more sensitive than a product list because the former contains personally identifiable information (PII), which is subject to privacy laws. The product list is probably already public, so breaching it means nothing.
The reason for this ranking is to prioritize protection. It’s impossible to apply the same level of protection to every data set. In this context, consider that data sensitivity and value may differ. Intellectual property (IP) data supporting your next patent could be worth billions of dollars. The business impact of an IP breach would be immense, so your IP might require the highest level of defense.
#3 – Access Control Policies
Who can access each data set? That’s a critical part of the data security policy. You already have some sort of access control mechanism in place, but you will likely have to adapt it to the data security policy. This may be because access is typically granted in your organization by network segment or application, not data. However, as data becomes subject to higher levels of protection, you will want to map access rights with data sets.
Indeed, you may already be working on some version of data-driven access controls if you’re implementing zero trust (ZT). ZT allows for granular grants of access down to the level of individual files, if necessary. If your organization is doing ZT, it’s a good idea to bring them into the process of developing the data security policy.
The best approach may be to use role-based access controls (RBACs), e.g., if your role is “Accounting Team Member,” then you should be allowed to see data that lets you do your job on the Accounting Team but not data for the Sales Team, and so forth. Defining and enforcing access control policies will invariably require using an identity and access management (IAM) system, such as Microsoft Entra ID, and SaaS security solutions like Suridata.
#4 – Real-Time Threat Detection
One of the more troubling aspects of serious data breaches is that attackers may be able to lurk inside your networks for months before being detected. A data security policy should mandate real-time threat detection. The goal is to prevent data breaches by responding to threats before they can cause too much damage. In some attack scenarios, such as ransomware, seconds count. The faster you can shut down an infected endpoint or stop ransomware from encrypting data, the more effective your data protections will be.
#5 – Misconfiguration Management
Software configurations, particularly in SaaS, can expose data to risk. For example, a SaaS app may allow public document sharing by default. This is an insecure configuration, one that needs to be hardened to prevent data leakage. However, keeping track of configurations across multiple SaaS apps can be difficult, especially considering that people outside of IT and Security can change their SaaS settings. An automated misconfiguration detection and remediation solution is essential for mitigating configuration risk.
#6 – Third-Party Integration Monitoring
Third-party applications can be a source of data risk exposure. With SaaS, for example, third-party plugins enable external apps to be treated as “users” of SaaS apps that contain your data. Your SaaS environment might have dozens or hundreds of such connections, any one of which could be insecure. The plugins themselves tend to be uneven in terms of quality and maintenance. For these reasons, the data security policy should incorporate third-party integration monitoring.
#7 – Data Encryption Standards
Some think that encryption is the only countermeasure required for data security. In reality, encryption is your last line of defense. Working from your data inventory and risk assessment, your data security policy should ensure that the most sensitive and valuable data sets receive the right levels of encryption. Again, with the sprawl of SaaS, you may leave some data unencrypted and at risk.
These seven are “must haves,” but there are more. Backup and recovery are important for ensuring data security. Incident response matters, as do audit logging and monitoring. And, while it’s not always the most effective way to defend against cyberattacks, employee training can help protect data. When employees understand, for instance, that they should not store sensitive data on public file drives, that can help avoid data security incidents.
How to Build and Implement a Data Security Policy
Realizing a data security policy means running herd on a variegated set of documents, programs, and people—especially people. Making a success of a data security policy is a human-centric activity. An effective data security policy will comprise people and organizational units who understand their roles in the policy and their responsibilities for policies and processes.
Practically speaking, a data security policy is like any other serious, large-scale security or governance program. It starts with a discovery and consensus-building process, followed by assignments of responsibility, with executive leadership and accountability at individual and team levels. It’s an ongoing workstream with regular assessments, course corrections, and updates.
The choice of tools matters. Suridata can help with the SaaS dimensions of a data security policy. The platform can automatically discover sensitive information across the SaaS ecosystem. It monitors SaaS apps for misconfigurations and automatically flags them for attention or automatically remediates them. In parallel, Suridata detects anomalies and policy violations, including external and anonymous data shares, which can be harmful leaks of important data, even if they are inadvertent.
Getting to a Successful Data Security Policy
Your organization needs a data security policy. The growing volumes and diversity of data, coupled with the cloud’s endless and hard-to-track potential for data storage, make data protection a high priority. The worsening threat environment and strict regulations affecting data make the matter all the more urgent.
However, a data security policy is only as strong as the tools and processes supporting it. Getting it right means embarking on a multi-step journey that includes action steps like building a comprehensive data inventory, conducting a risk assessment, evaluating and updating access controls, and more. Much of the time, the foundational elements of the data security policy already exist, but they need to be adapted for the policy. People are essential to success, too. Clear roles, responsibilities, and accountability will enable what can be a complex set of policies to come together to protect sensitive data.
Suridata provides you with the ability to proactively address the “must-haves” with its advanced SaaS scanning, detection, and monitoring capabilities.
To learn more about how Suridata can help you operationalize your data security policy, schedule a demo.