7 GitHub Security Best Practices for 2024
Is it a coincidence that the mascot for GitHub, the world’s largest source code host, is cat? Probably not, given that managing software developers is often likened to herding cats. Although now owned by Microsoft, GitHub is at the core of most open-source software development projects, with over 400 million code repositories and 100 million developer users. Thousands of major enterprises rely on GitHub as a developer platform.
In functional terms, think of GitHub as a software-as-a-service (SaaS) application, albeit one that comes with some serious security challenges. Hackers love GitHub because it contains so many keys to so many different kingdoms. It’s home to all sorts of login credentials for sensitive networks. Mostly, though, GitHub represents an amazing platform for launching supply chain attacks. By implanting malware-laden code components in GitHub, a malicious actor can easily seed thousands of development projects with unseen trap doors.
Attacks on GitHub have become common, but uncommonly sophisticated and potentially devastating. GitHub leaked more than 12 million authentication secrets and keys in 2023 alone. Then, just last month, attackers used stolen cookies to hijack GitHub accounts and gained the ability to inject malicious code into trusted repositories.
What is GitHub security?
Given the value of GitHub as a target, it should make sense that you need to take steps to defend your GitHub instance. GitHub itself offers numerous security features to help in this workload. Third-party tools can be useful, as well. Most importantly, however, it’s necessary to recognize the risks inherent in using GitHub and plan carefully to mitigate them.
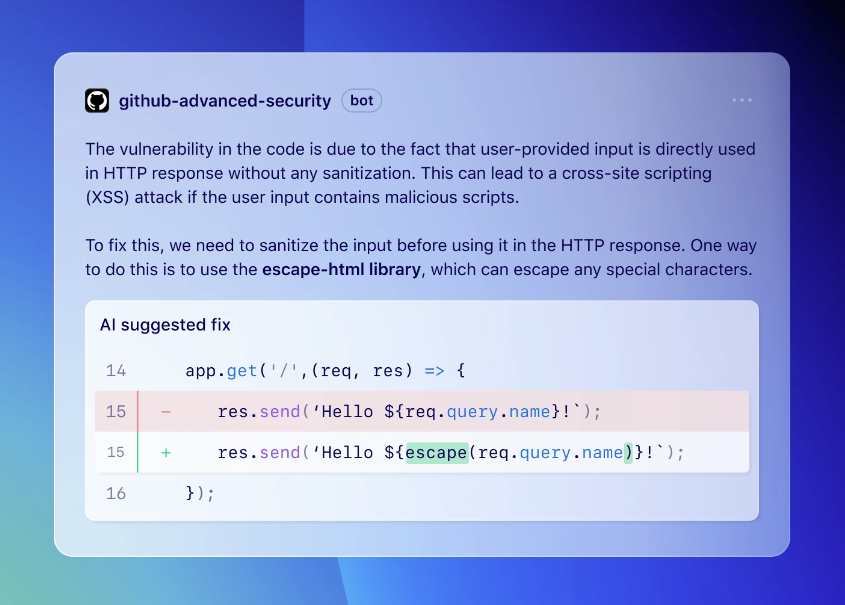
Why you need to invest in GitHub security
GitHub should be a priority for investments in security due to the central role it plays in application development. Not only is GitHub usually home to all sorts of valuable source code and internal documents, and credentials, it’s also ground zero for supply chain attacks on your organization. And, multiple teams typically access and collaborate on GitHub for version control—a formula for cyber vulnerability. 7 GitHub Security Best Practices for 2024 | Suridata
GitHub may already be part of your security program, especially if your organization has implemented application security (AppSec) countermeasures at the development stage or if it is doing DevSecOps. Even if you are “shifting left” in this way, though, you might still want to pay extra attention to GitHub, given its potential for risk exposure at the development stage.
Indeed, it might be better to think about GitHub in terms of SaaS security. It’s most likely one of hundreds of SaaS apps that your organization is using, but perhaps you haven’t thought about it that way. It’s deep in the recesses of the IT organization, not a production app like Salesforce or Microsoft 365. So, you may not apply SaaS security to GitHub, but you might want to consider doing so.
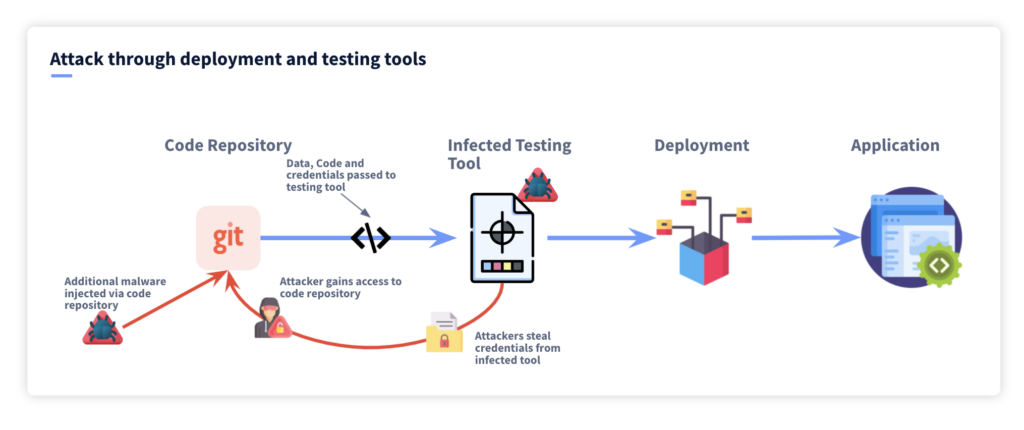
The Security challenges of GitHub environments
Securing GitHub environments brings its share of challenges, especially considering the integrated, collaborative nature of the platform and the many different people and teams who use it. The fact that most users are developers compounds the challenges. They may de-emphasize security as a concern or neglect to follow security policies that interfere with their personal productivity (See: Cats, herding).
Challenges include:
- Staying on top of access controls and permissions—Who can access GitHub, and what can they do once they’re on the platform. GitHub may not integrate/federate with your identity and access management (IAM) solution, so it can be hard to know who is who and who can do what.
- Keeping third-party integrations secure—GitHub integrates with hundreds of other applications, from IT ticketing systems to work tracking tools and beyond. These third-party integrations can expose GitHub to risk, particularly the risk of unauthorized access.
- Protecting the organization from GitHub-based phishing and social engineering attacks—The community-centric nature of GitHub users, who may span different entities, makes phishing and social engineering a serious risk. Will you be able to tell if one of your user accounts has been compromised?
- Avoiding misconfigurations that affect security—GitHub configurations can affect security. For example, applying proper Branch Protection Rules to ensure that new code is integrated only after it was checked and reviewed. Or, enabling GitHub built-in capabilities for scanning, identifying, by alerting on vulnerable dependencies within your code, as well as on possible secrets (i.e. passwords, tokens, etc.) that were accidentally placed within your code.
- Protecting sensitive data stored in GitHub repositories—Are GitHub users storing data that hackers want, like log in credentials and keys? How would you know if they did?
7 Essential SaaS Security Best Practices for GitHub
There are a number of SaaS security best practices you can adopt If you want to be serious about securing GitHub, either on its own or as part of a broader AppSec or DevSecOps initiative. Some are based on GitHub’s own extensive built-in security features. Others use third-party solutions. Others, still are policy or process based.
Here are 7 to consider:
#1: Enable MFA for GitHub Accounts
MFA is an excellent countermeasure that cuts down on the chances of an unauthorized person gaining access to your GitHub environment. GitHub is on this, requiring two-factor authentication (2FA) using a time-based one-time password (TOTP). Many third-party solutions can also make this work, including Duo and Google Authenticator. One recommendation is to use an authenticator app versus SMS/Text messages for TOTP, due to the risk of simswap attacks that let hackers breach a GitHub environment even with MFA in place.
#2: Enforce Strong Passwords and Regular Updates
Strong passwords will help reduce the risk of unauthorized logins based on brute force attacks. Overall, though, GitHub requires a set of password policies, such as requiring regular password updates and strict rules against sharing passwords. It may be optimal to implement single sign on (SSO) and make access to GitHub subject to organization-wide access control policies and password rules.
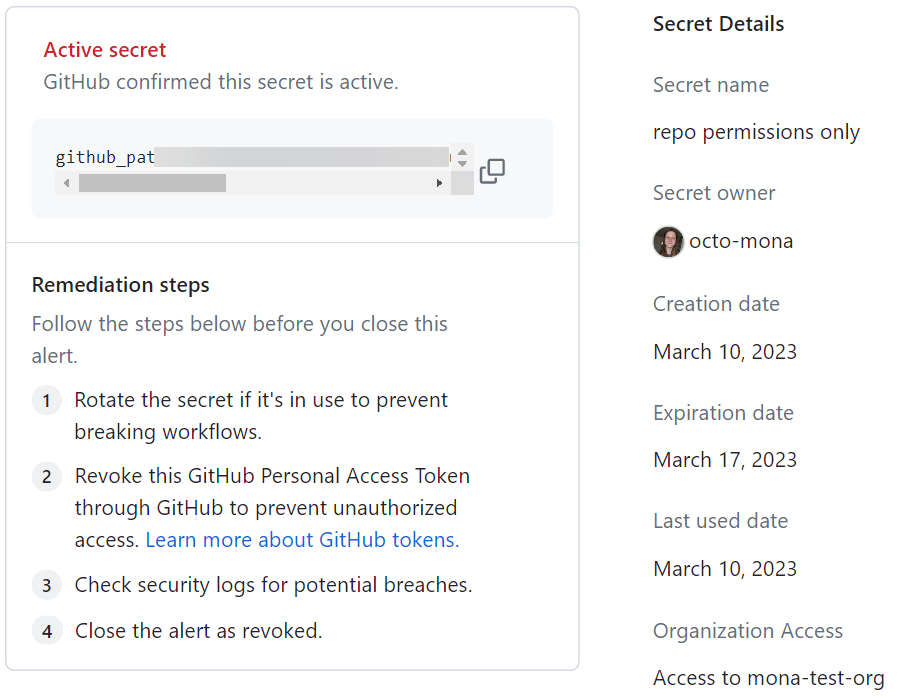
#3: Activate GitHub Secret Scanning
GitHub enables you to scan your repository and search for secrets that should not have been stored there. For example, a GitHub user might add a security token or private key in a repository to make his or her life easier when dealing with application integration. However, this practice leaves these secrets vulnerable to breach, leading to more potential risk exposure. The GitHub Secret Scanner reviews the entire Git history on all branches and scours it for secrets.
The GitHub scanner has a relatively narrow focus, however. It mostly looks for known string structures like API Keys—possibly missing password, admin URLs, and so forth. A third-party tool like Suridata’s SaaS security solution can be configured to scan for a much wider range of data hidden in massive GitHub repositories. A further best practice, which should ideally be a policy, is to replace any secret that has been made public. You should assume that it was discovered by someone and that is has been compromised.
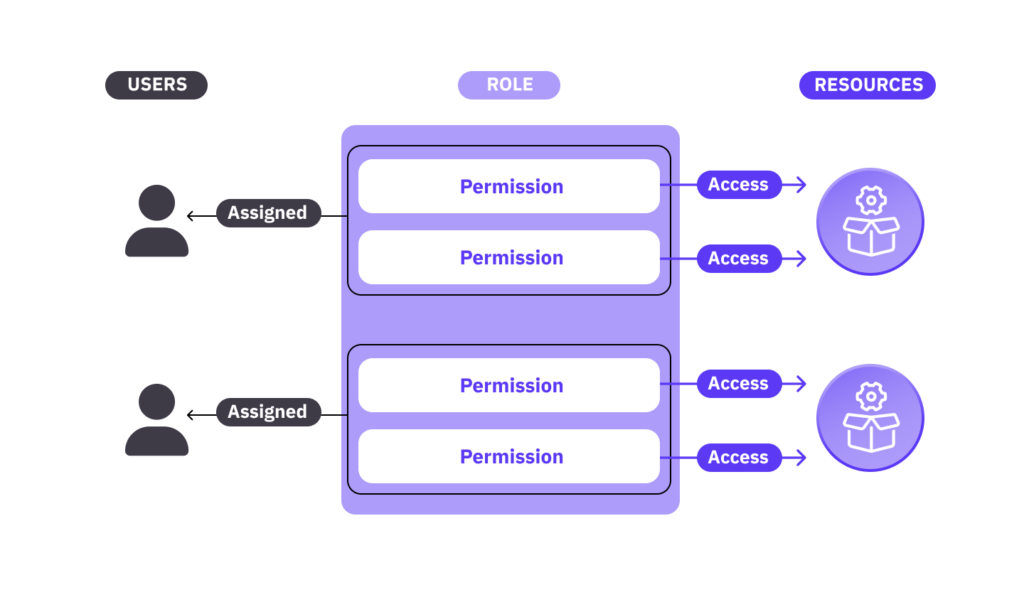
#4: Apply Least Privilege Access Controls
Code in GitHub is vulnerable to manipulation by malicious actors, e.g., implanting malware-laden code into your codebase, it is a good practice to limit access privileges by default. The fewer places in GitHub a user can go, the better. This means putting the principle of least privilege (PoLP) into effect. GitHub offers five levels of access privilege: Read, Triage, Write, Maintain, and Admin. By applying PoLP, you can limit users to the lowest level of privilege they need to do their jobs. As a result, your repositories will have less risk of accidental exposure of sensitive data as well as intrusions by hackers.
#5: Monitor Access Logs for Suspicious Activity
The sophistication of the March, 2024 GitHub attack, which involved inserting malware-infused copies of the popular Colorama tool in GitHub, shows how difficult it can be to detect attacks and prevent hackers from penetrating GitHub. To mitigate this type of risk, the best practice is to monitor GitHub’s logs, including access logs, for suspicious activity. Anomalies in access, such as users logging in from foreign countries or stolen cookies appearing on two devices at the same time, could signal the start of an attack.
#6: Implement Branch Protection Rules
This is not a SaaS security practice, per se, but it’s still quite important for the security of code that resides in GitHub repositories. When a user can create a branch, that enables him or her to create a new version of a code component. This may not sound like much of a risk, but if the user is a malicious insider, he or she can implant malware into the new branch, which can then go into production. GitHub has a variety of branch controls, including the ability to lock branches, restrict the merging of branches, and restricting branching privileges to certain users.
#7: Back Up your GitHub
Your GitHub data is precious. It represents intellectual property, many person-hours of work, and, in some cases, the digital core of your entire business strategy. You need to protect that data from attack, especially ransomware attacks. Even a simple outage can cause serious problems. GitHub has its own backup feature, Git CLI, but third-party vendors like Veeam support GitHub backups as well and make GitHub backup part of a broader enterprise backup process. One challenge to deal with, however, is the risk that a backed-up version of a GitHub repository will itself become a target of attackers.
Onward to a More Secure GitHub
GitHub may not seem like it’s part of your SaaS ecosystem. It’s not an operational app or software your people use for general business productivity. However, structurally, and in all the most important senses, GitHub is very much a SaaS app. It’s web based. It’s accessible by browser from anywhere, on any device. It contains valuable, often sensitive data. As such, it should be subject to SaaS security countermeasures and controls.
SaaS security best practices for GitHub encompass standard SaaS security controls like MFA and strong passwords. It’s also wise to apply best practices that are specific to GitHub, such as secrets scanning and enforcing policies that limit the risks of branching. If you approach GitHub with these best practices, you should be able to improve your application security posture by making your software development processes more secure.
To learn more about how Suridata’s SaaS security solution can help with GitHub security, visit www.suridata.ai or book a demo.
Co-Founder & CPO
