7 Essential SaaS Security Best Practices

If your organization is like most, you probably use over a hundred SaaS applications. SaaS apps offer convenience, instant access to pre-built and easily deployable features, and flexibility to meet changing business needs. However, the more SaaS apps you connect to, the bigger your security gaps.
58% of organizations estimate their current SaaS security solutions only cover 50% or less of their SaaS applications. Even if you have robust controls and cybersecurity technologies on-premises and in the cloud, they are unlikely to cover the usage of your SaaS apps.
What is SaaS security?
SaaS security comprises a collection of controls, policies, and practices to protect SaaS data and systems. Each SaaS app typically has its own security controls, many of which end users can configure. This flexibility opens the door to various security gaps and misconfigurations, which can be used to launch cyberattacks. This challenge is exacerbated by the fact that users can access SaaS apps from devices anywhere in the world.
Until recently, companies have been able to live with the SaaS tradeoff: you get the benefits of SaaS, but security can be a troubling afterthought. However, rising SaaS threats like ransomware, Cross-Site Scripting (XSS), and Man-in-the-Middle (MitM) attacks are pressuring IT managers to improve their SaaS security strategy.
SaaS security in 2024: The top challenges
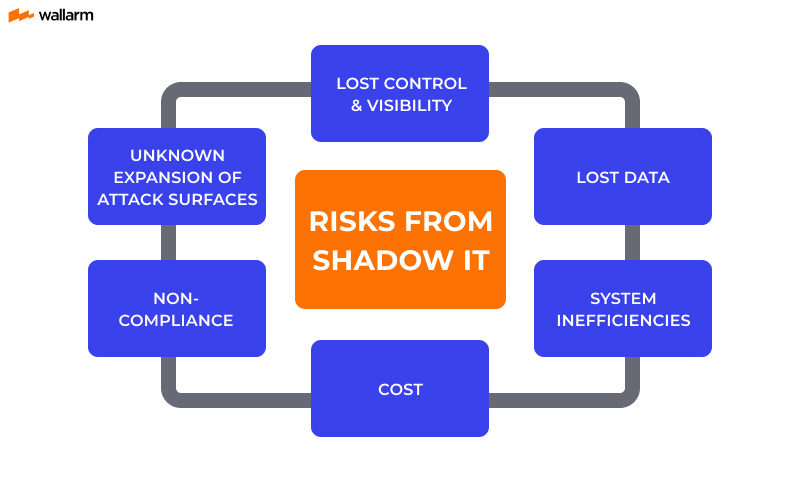
1. Shadow SaaS
Shadow SaaS, a subsegment of Shadow IT, refers to employees using SaaS apps without IT approval or awareness. For example, employees may set up a SaaS account using a credit card and add corporate data to that app without notifying the IT department or security team.
It’s a highly problematic occurrence, as it can lead to data breaches, loss of confidential data, and exposure to cyber-attacks. Plus, because the relevant teams are unaware of the usage of this app, response to potential vulnerabilities may be delayed.
2. Insecure SaaS configurations
Each SaaS app is hosted and managed by a separate company, so it can be configured separately. The end user can often choose how to configure their security settings. Without appropriate security training, employees may unintentionally set up the wrong configurations and open doors to data exposure or unauthorized access. Other misconfiguration risks include not updating the app’s default settings, permitting easy-to-guess passwords, and not requiring Multi-Factor Authentication (MFA).
3. Lack of visibility into third-party risks
SaaS apps are often integrated with third-party systems, including other SaaS apps. These integrations, typically done with plugins, are a significant source of SaaS risk. Malicious actors can use vulnerable plugins to penetrate SaaS apps, steal data, or damage the system.
Gaining complete visibility into your vendor’s systems and other connected third parties is challenging. However, companies can remediate this lack of transparency by implementing robust third-party risk management. This strategy ensures vendors have the tools and processes to restrict user access, protect user data, and comply with relevant regulations such as GDPR, SOX, HIPAA, or CCPA.
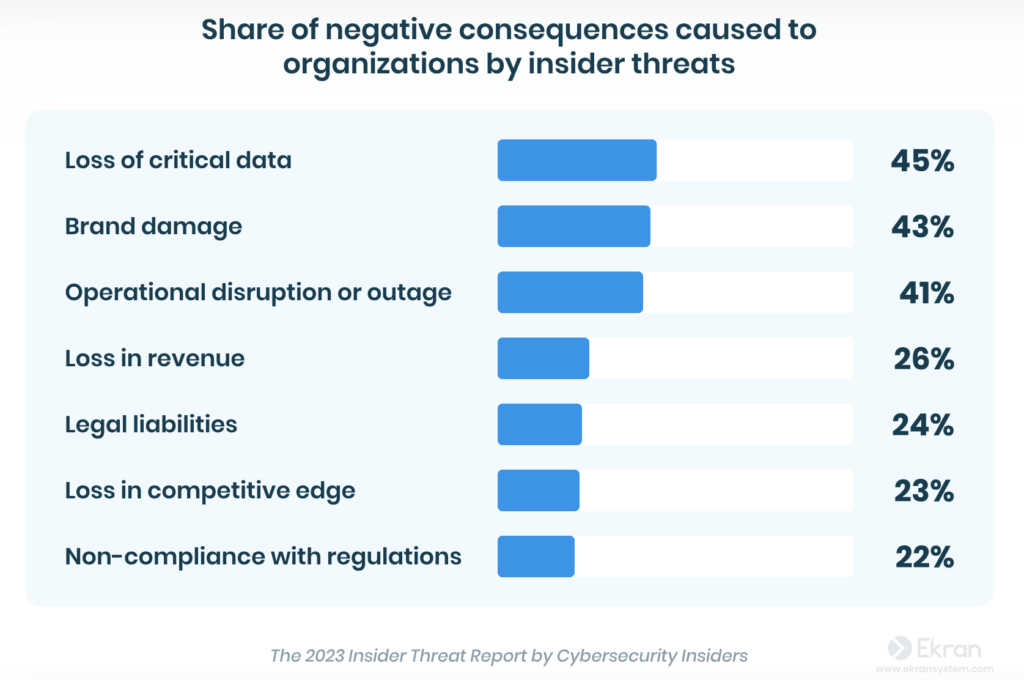
4. Insider threats
Employees can pose a threat to your SaaS security as they can to other digital assets. The difference is that with SaaS, it can be much harder to track who is doing what, and insiders can exfiltrate data before anyone finds out. Sometimes, the threat is accidental, such as when an employee moves data to a SaaS app without realizing it’s against the company’s policy. In more extreme and infrequent cases, disgruntled employees may misuse their access to seek revenge and sabotage systems.
5. Potential compliance violations
If your organization doesn’t have visibility into corporate data stored on SaaS apps, it risks violating regulations and industry frameworks that protect consumer privacy. Some of the most notable regulations, like GDPR, CPPA, and PIPEDA, require proof that you have the security tools and systems to protect user data.
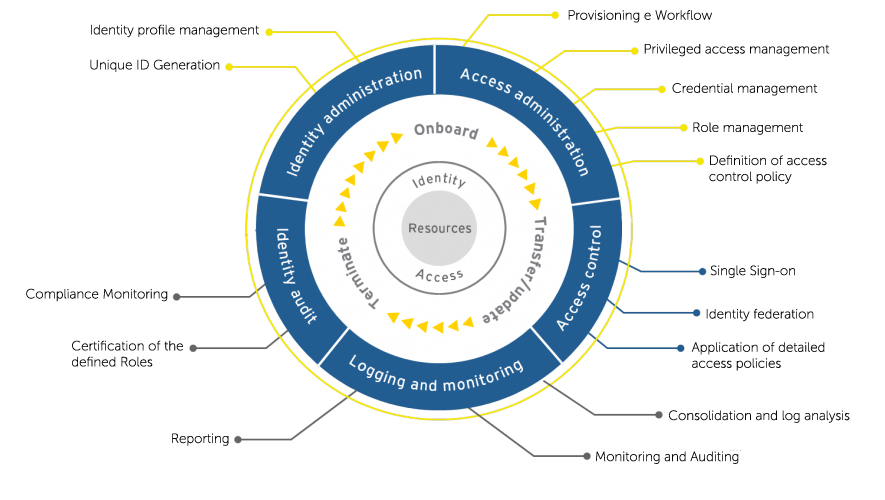
6. Poor access control management (IAM)
Without centralized identity and access management (IAM), SaaS users log into each app’s separate access control system independently. You can quickly have a situation where a hundred SaaS apps comprise a hundred different access management systems, and it becomes impossible to know who has access to what. One of many risks inherent in this scenario is unintentionally enabling former employees to still log in to your apps and get their hands on confidential data.
7 Essential SaaS Security Best Practices
1. Implement Centralized User Authentication and Access Controls
Your SaaS security posture will improve dramatically if you can control who has access to each SaaS app and what privileges they have once logged into it. Integrating your IAM solution into each SaaS app will enable you to build a unified identity governance framework and centrally define access rights and privileges. For example, you could integrate Microsoft Active Directory with Salesforce.com, Workday, or HubSpot. Alternatively, you could deploy a purpose-built solution.
2. Scan (and train) for Shadow SaaS
Shadow SaaS creates risk exposure across multiple dimensions. Employees may place sensitive data on SaaS apps without proper controls, or they may not set up adequate security protections, like MFA and data encryption. Worst of all, no one in IT or security knows about it.
Training can help reduce the potential for Shadow SaaS to occur. While it isn’t a bulletproof solution, it is wise to make employees aware that setting up their own SaaS accounts is a bad practice. Continuously scanning for Shadow SaaS is an even better solution. Using specialized tools like the Suridata SaaS security platform, you can monitor endpoints for activities that reveal the presence of Shadow SaaS accounts. The platform can then alert the right people and recommend remediations.
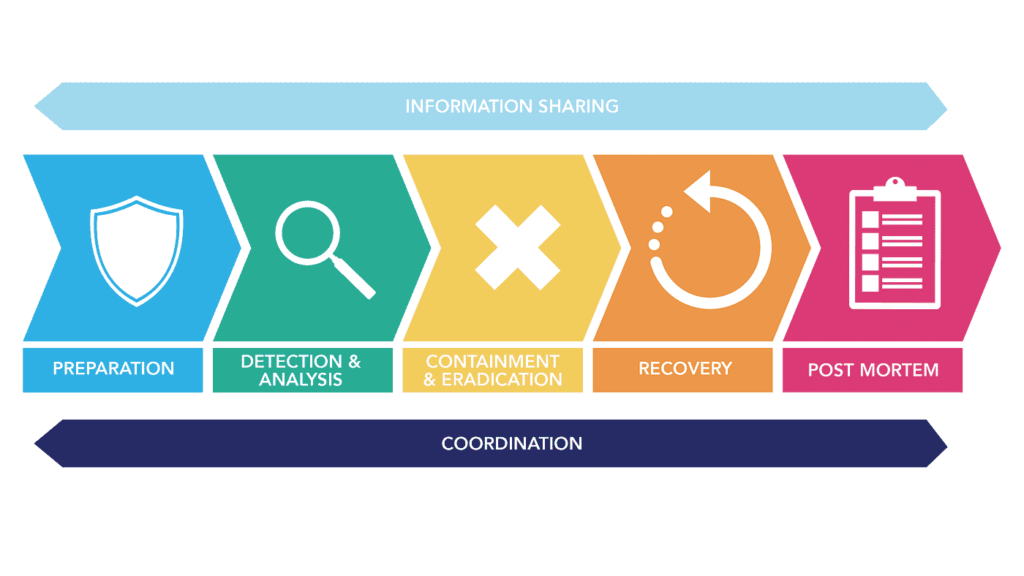
3. Include SaaS in Your Security Incident Response and Recovery Plans
Suridata’s research revealed that 88% of organizations have had a SaaS security incident. Even if you’re part of the lucky 12%, you should still adopt preventative cybersecurity controls and ensure you can respond and recover from a security incident should it occur.
The Security Operations Center (SOC) team should create an incident response playbook for a SaaS security incident. The playbook, which could be entered into a Security Orchestration Automation and Response (SOAR) solution, might include steps like isolating affected endpoints, contacting the SaaS provider to determine the cause of the incident, tracking the vendor’s recovery efforts, and notifying internal stakeholders like your legal department.
4. Conduct SaaS Vendor Security Assessments
Subscribing to a SaaS app is more than just a technology integration- it’s a business relationship. You’re working minute by minute with another company, often with your most critical information assets at stake. You want to work with the right SaaS vendors and trust them to protect your assets.
For this reason, it’s a best practice to conduct a SaaS vendor security assessment as part of the procurement process. You could ask the vendor for specifics on securing their data centers and infrastructure, encryption and MFA options, or whether they have passed a SOC2 audit and other key certifications.
5. Vet Your Third-Party SaaS Integration Plugins
Third-party integration plugins are a potential source of vulnerability, so it’s wise to vet these plugins for security. You will want to look at factors like the level of support, security features like data encryption, and data storage and retention practices.
Sometimes, a software company releases a SaaS plugin but then abandons it. Eventually, this plugin will get outdated and insecure. Even just looking at a plugin’s age may inform your decision on whether or not you should integrate it into your software. If a new version of this plugin hasn’t come out in about three years, it may be best to raise some questions and consider your decision further.
6. Continuously Monitor Your Entire SaaS Environment
One of the biggest problems in SaaS security is a lack of visibility into what’s happening across multiple SaaS apps. A vital best practice is to implement continuous monitoring of the entire SaaS environment. This might mean monitoring user sessions to detect suspicious activities and verifying that third-party integration plugins are secure or that security configurations are not creating risk exposure.
Due to the extensibility of your SaaS apps, it’s virtually impossible to monitor this activity manually. Therefore, you should consider using a comprehensive SSPM platform or equivalent.
7. Map SaaS to Your Compliance Programs
SaaS must be part of any compliance process involving financial transactions, health information, and privacy. Compliance teams should know where SaaS apps store data relevant to regulations and industry compliance frameworks like PCI-DSS.
SaaS system owners also need to understand where their apps intersect with compliance. For example, a SaaS-based Enterprise Resource Planning (ERP) application may be subject to rules regarding financial controls, which prevent the same user from issuing a purchase order and approving a payment to that vendor. In that case, the SaaS owner must show that user permissions on the app adhere to such controls.
Getting Started in Securing Your SaaS Apps
The risks of a data breach or comparably bad incident are too high for SaaS security to be neglected. Centralizing user authentication and access controls, continuously monitoring the entire SaaS environment, and protecting your SaaS data through encryption are just some of the steps you can take today to fortify your SaaS security posture.
Tools like Suridata can help you gain visibility across all your SaaS apps, enabling you to spot hidden misconfigurations and vulnerabilities and address these in real-time. By automating SaaS monitoring, threat detection, and response, you can take a proactive approach to SaaS security and develop a sustainable and efficient remediation plan. Request a demo here.
Co-Founder & CPO
