What is the Microsoft Teams Vulnerability and 6 Precautions You Need to Take
Admit it: You’ve recently worried about your hair on a Microsoft Teams call. As one of the world’s most widely used collaboration tools, Teams is an essential platform for organizations worldwide. However, it is also a prime target for hackers who see it as a gateway into corporate networks, file repositories, and even a launchpad for impersonation and fraud.
The risks have only grown over the past few years. Microsoft is doing its part in tackling growing threats by blocking an average of 4,000 identity authentication attack attempts per second on Teams. Still, this app’s security has to be a joint effort. As a SaaS product, Teams operates under a shared security model where customers must also play a role in defense.
Explaining the Microsoft Teams Vulnerability
Microsoft Teams is an incredibly multifaceted platform. In addition to the standard voice and video functionalities, it offers project management, collaboration workflows, and integrations with the broader Microsoft ecosystem (think Outlook, Office, SharePoint, and Active Directory). Together, Teams and their integrated parts form a broad external attack surface.
Microsoft Teams vulnerabilities generally fall into two categories. The first allows attackers to bypass security controls and send files to external tenants—TeamPhisher is one example of this type of attack.
The second type concerns security managers and involves phishing schemes to impersonate executives. For example, an attacker could pose as the Chief Financial Officer to trick employees into wiring funds to fraudulent accounts.
Since users often perceive Teams as an internal-only tool, they may assume that all contacts are legitimate employees, amplifying the risk of social engineering attacks. This implicit trust within Teams is what makes exploits like TeamPhisher particularly dangerous.

The Impact of Microsoft Teams Vulnerabilities for Businesses
Attackers who can gain access to Teams have the potential to carry out a wide range of destructive acts, including:
- Malicious Code Execution—Attackers can exploit the insider network access provided by penetrating Teams. For instance, they could mount malicious code execution attacks, injecting code into a system to disrupt it or extract sensitive information.
- Data Breaches and Information Theft—Because Teams users are generally assumed to be authorized insiders, an attacker posing as a Teams user can access data and files from the inside. They may steal sensitive information, intellectual property, and information about other Teams users.
- Social engineering Attacks—When attackers access users’ personal information, they can use it to power more targeted and convincing phishing and social engineering attacks. By learning details like an employee’s pet’s name, they can impersonate someone from their inner circle, making the deception more believable.
- Exploitation of Privileged Accounts—An attacker who takes over a Teams account can exploit the victim’s access privileges. For instance, if the victim is an accountant, the attacker might be able to see financial reports stored in Teams. They can also escalate their privileges by contacting the IT department using Teams.
- Installation of Malware or Spyware—Bad actors can upload malware-laden files into Teams file repositories. These might include ransomware or spyware.
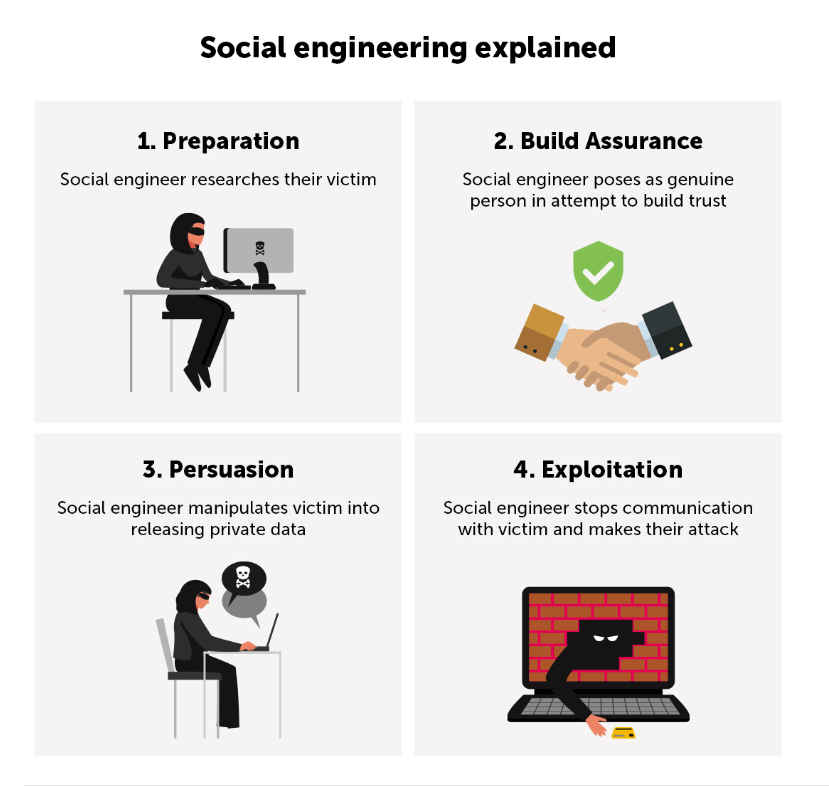
6 Precautions You Need to Take to Mitigate the Microsoft Teams Vulnerability
So, what can you do about the Microsoft Teams vulnerability? One thing to remember is that Microsoft itself shoulders a significant burden here. They are on task to identify vulnerabilities and constantly update the SaaS software. Microsoft also issues guidance on mitigating Teams risk. With TeamsPhisher, for example, the company advised Teams administrators to review settings and take actions that make it harder for an attacker to exploit the vulnerability.
However, you must take some responsibility, too. Here are six actions you can take to secure your Teams platform:
1. Restricting External Access to Protect Shared Channels
Limit external access by adjusting settings in the Teams Admin Center. Start by blocking users from inviting external participants to shared channels, as these guests can read and write messages, creating a potential entry point for malicious actors.
Review and manage Teams’ external access settings for broader collaboration needs. If external access is required, restrict it to specific, trusted domains. Otherwise, set Teams to “Block all external domains” to prevent unauthorized access entirely.
You can also configure Teams so that unmanaged external users cannot initiate conversations with users in your organization. This control can reduce phishing attempts and unauthorized access.
2. Regularly Review User Permissions and Related Workflows
Companies like Teams because it enables seamless collaboration between employees, vendors, and contractors, but this openness also introduces significant security risks. A critical best practice for safeguarding access is to review user permissions regularly. For example, you may find that a freelancer who is no longer employed still has access to sensitive resources. Equally important is scrutinizing the workflow for granting and revoking access. Security lapses often occur when removing access from external users is overlooked or forgotten.
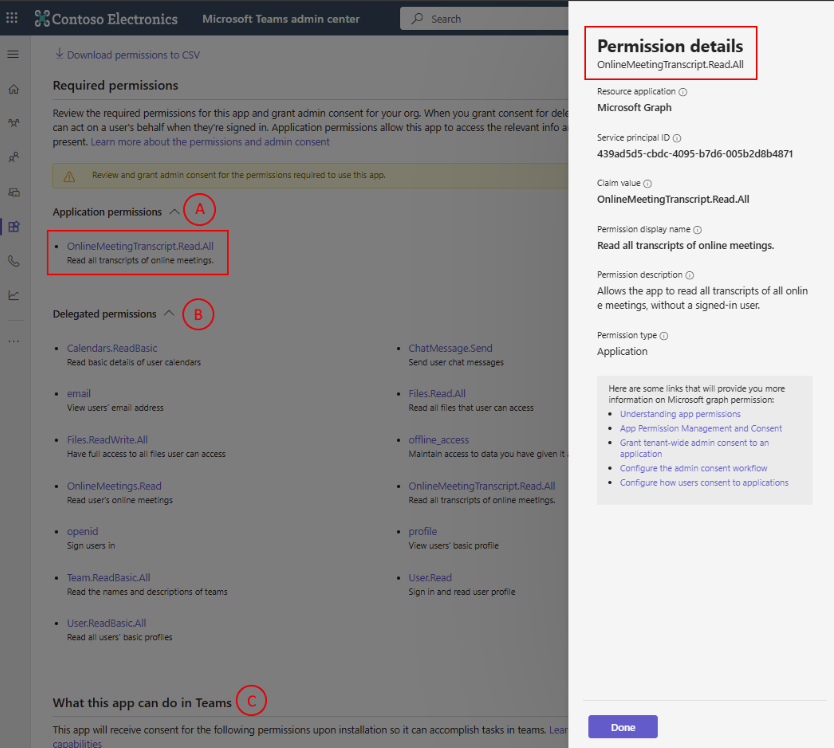
3. Train and Educate Users on Teams Security
Due to its collaborative features and file-sharing capabilities, Microsoft Teams is especially vulnerable to human error. A comprehensive training program can improve security by teaching employees safe data-sharing practices, spotting phishing attempts, and recognizing signs of compromise. Training should also include practical SaaS security steps, such as verifying unknown contacts before sharing sensitive information, reporting suspicious activity to IT, regularly updating passwords, and adjusting privacy settings to control external access.
4. Implement Conditional Access Policies
Limiting access to users who meet specified conditions, such as complying with MFA, helps reduce the probability that a malicious actor will penetrate Teams. Alternatively, conditional access policies can restrict the digital assets a user can access once he has gotten into Teams. He may not be permitted anywhere else on the network, which is good for reducing the risk of lateral movement.
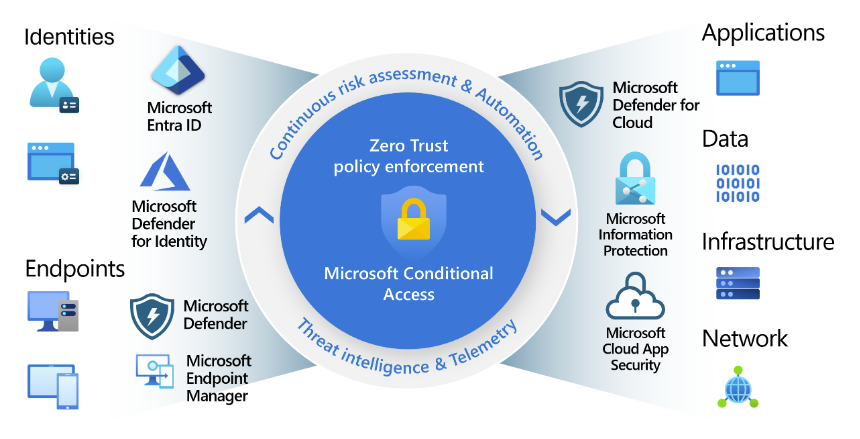
5. Monitor and Audit Teams Activity
Teams’ vulnerabilities and exposure to social engineering make monitoring and auditing user activity crucial. Suspicious behaviors (like sending the same file to many users across different departments) can signal a potential attack. Blocking such actions until further investigation can help mitigate risks.
Another effective measure is deploying Data Loss Prevention (DLP) tools. These tools track file transfers and other sensitive actions, providing real-time alerts when a data breach is detected, enabling swift intervention before damage occurs.
6. Monitor and Control Teams Integrations
Teams integrates extensively with the Microsoft ecosystem and various third-party enterprise applications. While this enhances productivity and streamlines business operations, it also increases the potential for security risks. Unmonitored integrations and insecure third-party plugins can open the door to vendor-related risks.
Monitoring tools like Suridata can help you mitigate these risks. These tools can continuously assess SaaS integrations for security gaps, flagging potentially unsafe third-party plug-ins and identifying other risk factors. Regularly reviewing and controlling these integrations ensures that only secure and necessary connections remain active, minimizing exposure to security breaches.
Getting the Team on the Same Page for Teams Security
There are no two ways about it—the Teams platform is vulnerable. From phishing attacks to exploits that enable unauthorized external access to Teams, the application exposes organizations to risk. However, it is possible to improve security for Teams if you take certain precautions, such as implementing conditional access rules, deploying DLP, monitoring integrations and activity for anomalies, and enforcing training.
If you want to fast-track and automate the security of your Teams platform – you should employ a specialized solution. SaaS security platforms like Suridata can monitor Teams user activity and inspect third-party integrations and configurations—flagging suspicious situations instantly and alerting security teams to remediate. Learn more here.
Co-Founder & CPO
