How to Perform an Application Dependency Mapping in 8 Simple Steps
Have you ever wondered why most enterprises schedule application upgrades at four o’clock on Sunday mornings? They do this in case the change “breaks” the application and causes it to cease functioning. Hopefully, an outage won’t affect many users then, and the upgrade team can either solve the problem or reverse the upgrade before it affects user experience.
But breakages aren’t a hypothetical issue. Three in four dependency vulnerability patches cause systems to break, often due to the unpredictable behavior of application dependencies. Application Dependency Mapping (ADM) is essential to addressing this risk.
Any stakeholder, from application developers to security teams and application admins, relies on application dependencies maps to anticipate issues and prevent security vulnerabilities arising from unexpected impacts of upgrades and changes.
What is Application Dependency Mapping, and How Does it Work?
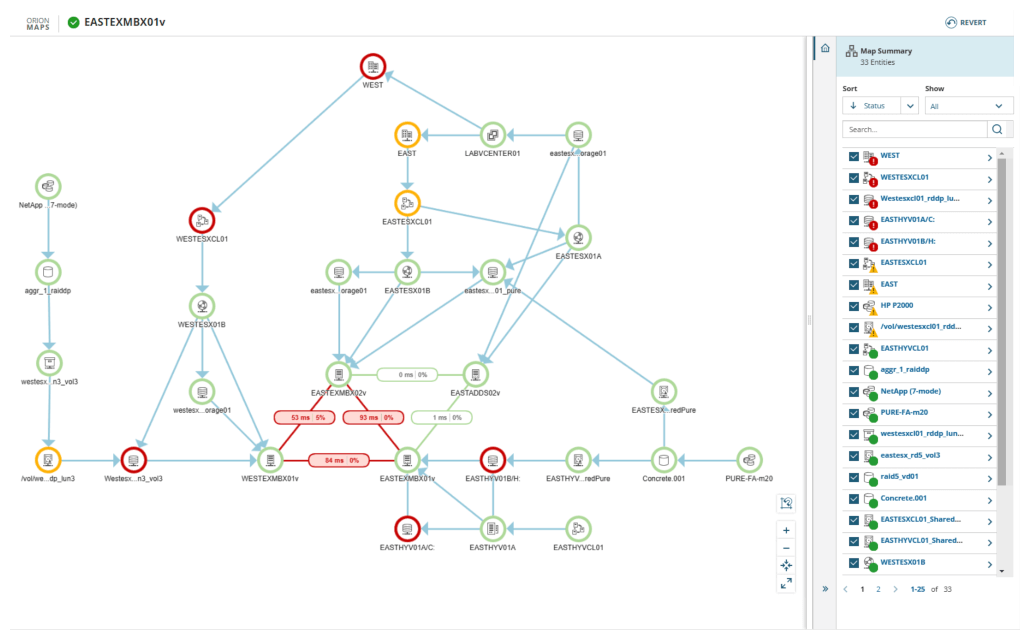
Application Dependency Mapping (ADM) visually represents the relationships between applications and sometimes their infrastructure, like servers or storage devices. Because these dependencies can introduce vulnerabilities, ADM is critical in enforcing a robust data security policy and helping teams identify and mitigate risks.
These dependency maps often use color coding or other visual cues to help stakeholders understand dependencies, their impact on security, and application reliability. Some maps even show data flows and dynamic interactions.
There are several ways to map dependencies. The simplest is manually drawing them with tools like Visio. Larger organizations use purpose-built tools that ping IP addresses, analyze network traffic, or install software agents to uncover dependencies. Application Performance Monitoring (APM) tools can also reveal relationships through performance data.
The growing use of SaaS applications complicates the ADM process. Pinging IP addresses and network monitoring are not viable methods to capture relationships between SaaS applications. Yet, SaaS apps often rely on each other in ways that impact security and performance. For example, a third-party integration plug can create a hidden dependency, potentially exposing both apps to data security risks.
Why Application Dependency Mapping is Essential in 2025
Application dependency mapping is critical for application reliability and maintaining a strong cybersecurity posture. While this has long been the case, it is more urgent than ever as supply chain risks are growing within application dependencies.
A recent example of this trend is the Okta breach in late 2023, where hackers compromised the support management system connected to Okta’s identity management solution to steal customer data. ADM could have helped security teams pinpoint such dependencies. Reasons why this process is essential today include:
- Enhanced Visibility and Risk Management—Application dependency mapping reveals connections that may be insecure and need remediation. Knowing where you have risk, you can manage it more effectively.
- Improved Incident Response—Knowing your application dependencies helps you respond faster to security incidents. If one application depends on another, you can quickly identify potential gaps in that dependency that may have caused the breach and remediate them.
- Faster, More Predictable, and Secure Change Management—An application dependency map highlights potential issues during a change process so you can address them beforehand. If problems arise, it helps you quickly troubleshoot the cause.
- Stronger Compliance and Auditing—ADM can aid compliance by making data protection and system integrity easier to achieve and audit. While not always required by regulations, several laws and frameworks mandate these practices, including GDPR, HIPAA, and NIST 800-53.
8 Steps to Perform Application Dependency Mapping
Setting up an application dependency mapping tool and letting it run is tempting, but that ignores some important bigger-picture issues and best practices. Here are eight steps that will help achieve the best outcomes from the ADM process.
#1 Step: Take a Phased Approach
If you’re new to application dependency mapping, starting with a subset of your IT estate is best. Not all applications and dependencies are equally critical, so begin by mapping those affecting your most business-critical applications, then expand to others in subsequent phases. Focus on high-risk areas, such as customer-facing applications or systems that handle sensitive data, to identify vulnerabilities quickly.
#2 Step: Inventory All Applications And Their Integrations
Even with a phased approach to ADM, it is wise to start with a complete inventory of your applications and their integrations, such as API connections. Integrations differ from dependencies, which can exist within applications or between software elements not captured in the integration inventory. Regularly update the inventory to account for new applications or integrations so your maps are always accurate and up to date.
#3 Step: Map Connections and Dependencies Between Applications
Links between applications can be challenging to identify, even for experienced professionals. This is due to the complexity of modern IT environments, which span both cloud and on-premises infrastructure. Use purpose-built tools, which save time and help uncover missing dependencies that are hard to spot.
For example, real-time dependency tracking and monitoring tools can update your maps continuously to reflect any changes in the environment, helping to catch new connections or vulnerabilities that may arise after initial mapping.
#4 Step: Leverage AI and Automation
ADM workflows are time-consuming and prone to error, but automation helps you move faster and build more accurate dependency maps. AI can also support this process, using pattern recognition and machine learning to identify dependencies and assess risk levels. Look for tools that integrate AI to flag high-risk dependencies.
Consider using GenAI to speed up report generation. GenAI can automate the production of dependency maps and accompanying documentation so your team can focus on analyzing the data rather than creating it.
#5 Step: Assess Risk Exposure Based on Dependencies
A dependency can expose your organization to risk, but not all dependency-related risks have the same potential impact on operations and security. Classify your assets based on their value and sensitivity, such as customer data, intellectual property, or financial records. Once you’ve identified your “crown jewels,” map out their dependencies via a detailed security risk assessment. These could be databases, third-party services, or cloud integrations.
#6 Step: Include SaaS in Your Map
Mapping dependencies between SaaS applications can be challenging, but it’s essential to understand how they connect and where data might be vulnerable to unauthorized access. Tools like Suridata can help by identifying misconfigurations, access tokens, API keys, and third-party integration plugins that introduce dependency-related risks. Suridata’s real-time monitoring of SaaS apps can also detect threats and attacks targeting these dependencies, even if they were not previously identified.
#7 Step: Integrate with Development
With continuous integration/continuous delivery (CI/CD), new dependencies appear multiple times a day. Therefore, it is essential to integrate ADM with development workflows to avoid falling behind. Automate the dependency mapping process within your CI/CD pipeline by integrating ADM tools with your version control and deployment tools. This ensures real-time updates to your dependency maps, keeping them in sync with the development cycle.
#8 Step: Test Dependencies and Update Maps Regularly
Dependencies tend to change, often rapidly. As a result, the dependency map from last year or last quarter is likely to be obsolete. Some dependencies are gone, while new ones have appeared as your cyber attack surface expanded. To avoid having an out-of-date map, it’s wise to test dependencies and update your maps regularly. Some ADM tools can do this automatically.
Keep in mind that ADM is a people-oriented organizational process. Developers, application owners, IT managers, security team members, and other stakeholders should know its importance. When you try to include stakeholders in the process, the map will be more accurate and impactful for everyone’s work.
Moving Toward Effective, Sustainable Application Dependency Mapping
Application Dependency Mapping (ADM) is key to identifying cybersecurity risks and ensuring application availability by uncovering hidden threats in application dependencies and interconnected SaaS environments. With the right automated tools, ADM becomes faster and more accurate, helping you prevent costly outages and data breaches. Suridata’s SaaS security platform can enhance your ADM efforts with real-time monitoring and automated detection of SaaS application integrations. Suridata turns complex data into actionable insights, strengthening your overall security posture.
To learn how Suridata can streamline your ADM processes, improve security, and support proactive management of SaaS-related risks, book a demo.
Co-Founder & CEO